 4 minutes
4 minutes
Implementing Zero Trust Security with Jakarta EE: A Practical Guide
Zero Trust security has moved from buzzword to necessity. The principle is simple: never trust, always verify. But implementing […]
In the fifth part of our continuing series on alternatives for commercial Oracle GlassFish features, we are looking at a replacement for the Oracle’s Access Manager integration feature.
{{cta(‘3382707d-3c20-4768-8acd-0a5b78c43d95’)}}
Oracle GlassFish Server includes a special security provider, implemented as a custom JASPIC (JSR-196, Java Authentication Service Provider Interface for Containers) module that allows enterprise applications to authenticate and take advantage of the Single Sign On functionality provided by its integration with Oracle Access Manager (a security suite with strong integration with other Oracle products and several infrastructure arrangements). This security provider can be used in the following 2 ways:
BASIC, FORM or client certificate (CERT) mechanisms; delegating authentication to the Access Manager.Since Oracle Access Manager is a proprietary licensed product of Oracle, there’s no special integration that comes bundled with Payara Server. However, Payara Server itself contains a simple Single Sign On solution inherited from GlassFish Open Source Edition that can be easily configured when using the standard JAAS configuration.
To enable this feature on Payara Server, go to the server-config → Virtual Server section and select the virtual servers used by your applications:
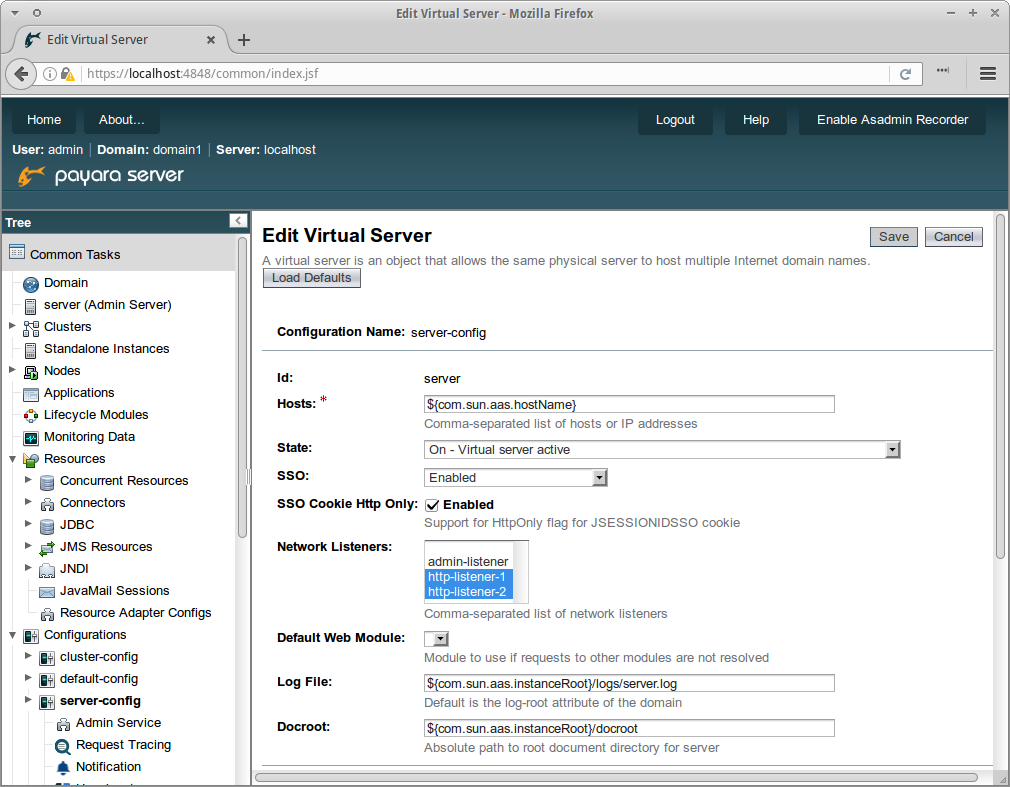
On the SSO property, select Enabled and configure the listeners that will be used for establishing the Single-Sign-On session (by default the standard HTTP and HTTPS listeners of the domain or instance configuration). Make sure to also set the sso-max-inactive-seconds and sso-reap-interval-seconds additional properties to the time frames that a SSO session will use before expiring.
When Single Sign On is enabled, all web applications that are deployed on the same virtual server will share authentication state, so if a user logs in to a web application he will be implicitly logged for all other remaining applications that require the same authentication information as well. Keep in mind that this behavior only applies for web applications configured on the same security realm.
If you were using Oracle Access Manager with your GlassFish Server and require a strong identity and access management suite of tools with good support that can be integrated with Payara Server, we strongly recommend migrating to ForgeRock’s suite of products and replace Oracle Access Manager with their own management suite.
Considering that the access management application (Open AM) doesn’t have direct support for Payara Server, to fully integrate it and its SSO capabilities, please follow the instructions we have detailed in our ‘Forge Rock Integration with Payara Server’ blog series:
 4 minutes
4 minutes
Zero Trust security has moved from buzzword to necessity. The principle is simple: never trust, always verify. But implementing […]
 3 minutes
3 minutes
When legacy systems approach end-of-life (EOL), enterprise IT teams typically face the choice of moving forward at all costs […]
 5 minutes
5 minutes
At Devoxx Belgium 2025, I was able to talk about what happens after you build your container. In theory, […]