The second episode in our ‘Quick Fire Java’ video series is out!
We discuss Log4j, security process and prioritization, and how Payara dealt with the vulnerability.
All in a concise 10-minute video.
TheLog4jvulnerability,Log4Shell, was disclosed in early December 2021 and the repercussions have been far-reaching.
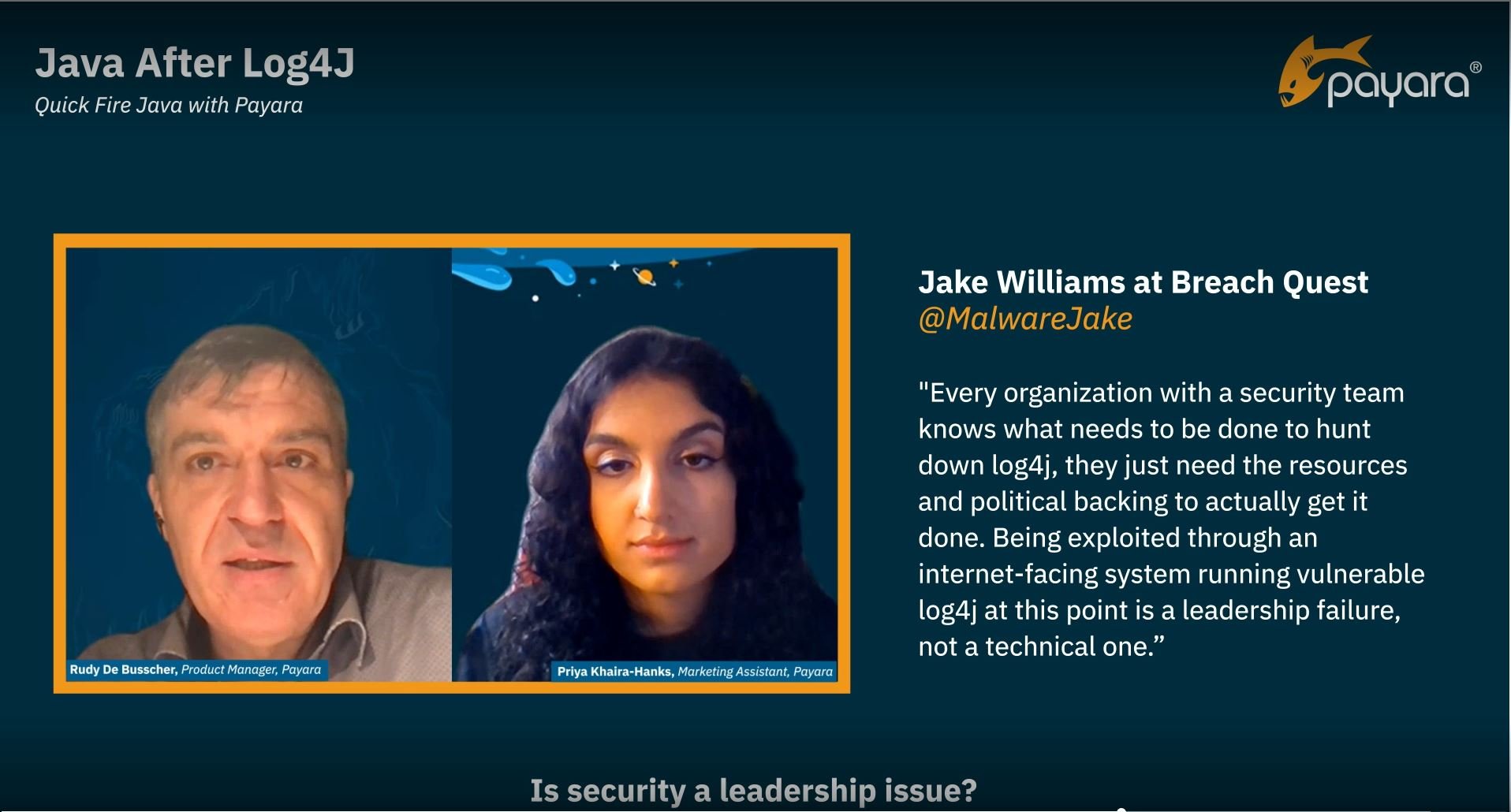
Rudy,ourProduct Managerat Payara, explains more about what this actually means and about the wider implications of the incident. He also responds toBreachQuest’sJake Williams for Threatpost, who claimed “being exploited through an internet-facing system running vulnerable log4j at this point is a leadership failure, not a technical one.”Watch the video to find out whether Rudy agrees.
It’s worth stressing that we have checked all Payara products and they are not affected by the vulnerability, but we recommend that you upgrade to the latest version of the library if you ARE using it. Read morehere.
Watch the video now:
This is the second in a series where we’ll ask key questions on subjects that matter to our community, for example aroundJava,Jakarta EE(previously Java EE), MicroProfile, DevOps, DevSecOps, database management and cloud. We’ll quiz an expert each month to create a concise 10-minute video.
Make Sure You Are Following Our YouTube for Updates:
 4 minutes
4 minutes