 3 minutes
3 minutes
What’s New in the January 2026 Payara Platform Release?
As we begin 2026, we’re pleased to announce new releases across all Payara Platform editions this January: Payara Platform […]
The HTTP Strict-Transport-Security response header (often abbreviated as HSTS) tells the browser that it should access the website only using HTTPS, instead of using HTTP.
The May 2021 releases of the Payara Platform, Community version 5.2021.3 and Enterprise version 5.28.0, allow you to configure the HSTS header.
What is the advantage of this header and why is performing a redirect to the SSL endpoint each time the user accesses your website not secure enough? We’ll explain these details and how you can configure the header in the Payara Platform products in this blog.
These days, a lot of websites already use the TLS protocol for secure connections that handle the communication between the server and the browser, or the client in general. The majority of websites use the TLS protocol due to the increased awareness around the importance of a secure connection, the many occasions where a hacker was able to mislead the user and retrieve personal information, and the availability of free and automated certificate authority like Let’s encrypt.
But the fact that the site uses a secure connection is not enough. Many times, the initial request to the Websites server is a plain HTTP request. The user has entered the website’s URL in the address bar of the browser and most people will just use http:// (rather than https:// ) or do not specify the protocol. This initial HTTP request still allows the attacker to intervene.
For example, when you enter the address of your banking application, the attacker, through a Man-In-The-Middle attack, can intercept this request and redirect you to his fake version of the application, retrieving vital information.
So how can we get rid of that first redirect to the SSL-based endpoint, avoiding the redirect and the fact that we, as users, are vulnerable?
As a user, you can make it a habit to always type the https in front of the URLs, or you can install a browser plugin that makes sure that only secure connections are used (by converting the http:// to https://). This plugin works well unless some site you visit does not support it. Therefore, the HTTP Strict-Transport-Security response header is a better solution and is defined on the server-side, indicating to your user base that you care about the security concerns. It is a specification (RFC 6797), so it works across all browsers and sites.
The server replies in a response to the client with the specific HSTS header:
Strict-Transport-Security: max-age=31536000;
The client, the browser in most cases, stores this information for further reference. The next time you access the same site, the browser only uses the secure option, even if you specify the plain HTTP protocol. The max-age option tells the client that a secure connection is forced in that time frame, and should be a minimum of 1 year (31536000 is the number of seconds and correspond with 365 days)
If you visit a website having this HSTS header, the next year the browser will never contact the host using an insecure protocol and thus not allow the attacker to redirect you to his malicious website.
This HSTS header is configured in most cases on the proxy server of your company which also handles the certificate and TLS options. In many cases, the boundary of your corporate network handles the SSL termination and can add the HSTS header to the outgoing response.
We have now added the possibility to add the HSTS header to the responses so that you don’t need to add it through a Servlet filter of your application.
The following Asadmin CLI command activates the addition of the header:
./asadmin set configs.config.server-config.network-config.protocols.protocol.${protocol-name}.ssl.hsts-enabled=true
From that moment on, each response will contain the header with a value for max-age that corresponds to 1 year. This period cannot be configured and will always be 31536000 seconds.
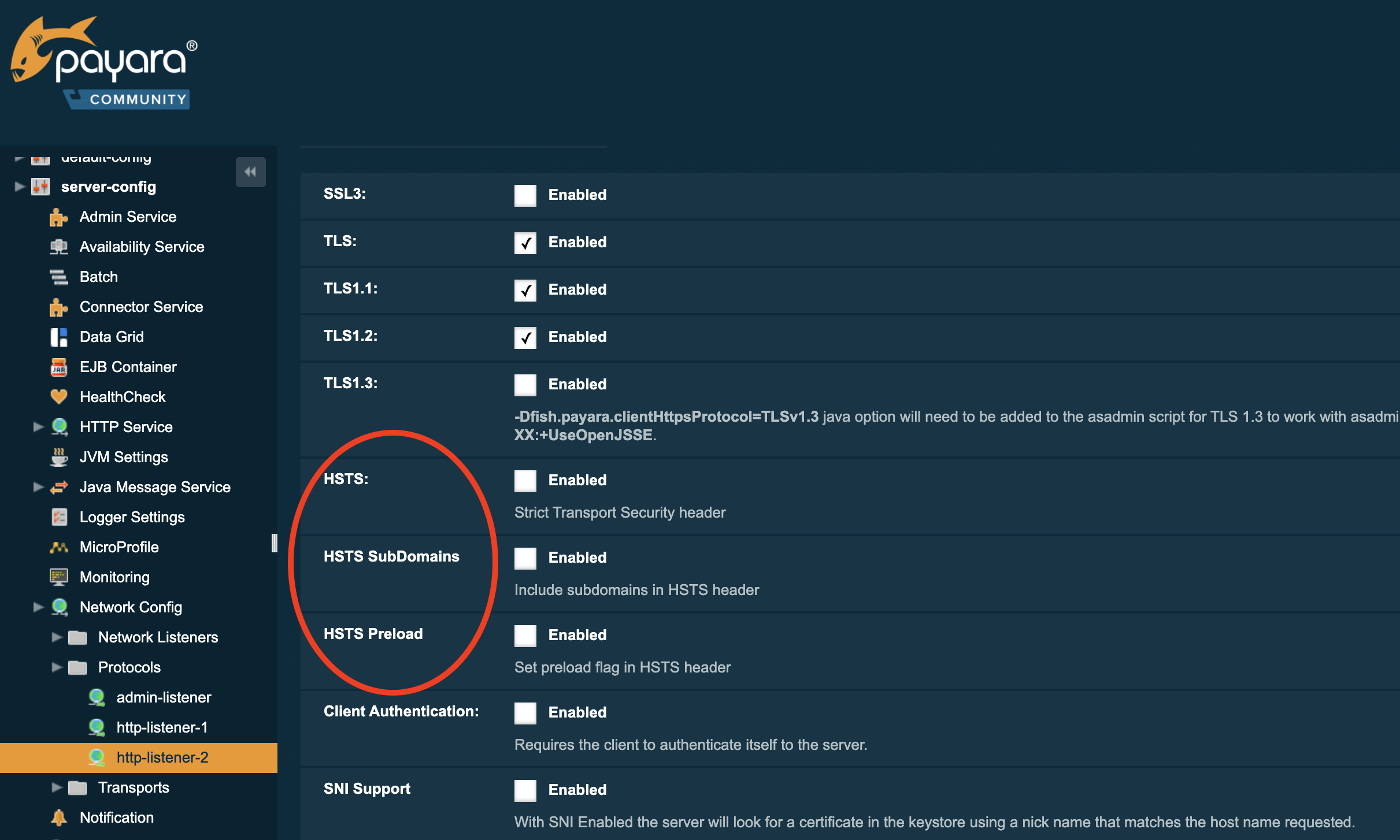
You can also use the Admin Console to activate this feature. Go to the SSL tab on the page server-config -> Network Config -> Protocols -> http-listener-2 Besides the max-age property, you can specify 2 other properties:
Besides the max-age property, you can specify 2 other properties:
– includeSubDomains
– preload
The includeSubDomains instructs the browser to use also an SSL connection for all subdomains. This allows the browser to immediately choose a secure connection when it needs to access a subdomain.
The preload option instructs the browser to send the domain to the central list of all domain names that support HSTS and that should be accessed only by SSL. This helps other people because the browser will immediately use a TLS based connection secure connection since the browser will find out that your website is on the centralized preload list.
With the May 2021 release of the Payara Platform, the Community version 5.2021.3 and Enterprise version 5.28.0 allow you to configure the HSTS header. Most of the time, this is configured on the proxy server but you now can do this on the Payara product itself without the need to write a custom Servlet filter. It allows to bypass the initial HTTP request many browsers make to your website and always use a secure connection avoiding a Man-In-The-Middle attack.
{{cta(‘b2e4c2b6-f33a-4ae4-9290-f1cf476f445a’)}}
Share:
 3 minutes
3 minutes
As we begin 2026, we’re pleased to announce new releases across all Payara Platform editions this January: Payara Platform […]
 3 minutes
3 minutes
The December 2025 releases bring targeted improvements and security updates across Payara Platform Enterprise versions 5.82.0 and 6.33.0 as […]
 4 minutes
4 minutes
Strategic acquisition bolsters Azul’s Java platform with complementary products, deep Java expertise and accelerated go-to-market capabilities SUNNYVALE, Calif., and MALVERN, […]
Hi
I am trying to enable hsts on Glassfish server.
./asadmin set configs.config.server-config.network-config.protocols.protocol.${protocol-name}.ssl.hsts-enabled=true
This command is showing error
asadmin> set configs.config.server-config.network-config.protocols.protocol.${protocol-name}.ssl.hsts-enabled=true
> set configs.config.server-config.network-config.protocols.protocol.sec-admin-listener.ssl.hsts-enabled=true
remote failure: Invalid name value pair set. Missing expected equal sign.
Command set failed.